Security Lifecycle Review is your simple guide to making your business systems more secure and efficient. Additionally, this article breaks down the full security process—from planning to monitoring—into easy steps.
Whether you manage a small company or a big organization, understanding this process helps you prevent cyber threats, stay updated with security trends, and protect your data.
By the end of this guide, you’ll know how a proper security lifecycle review can transform your approach to digital safety and long-term success.
Understanding the Security Lifecycle Review
A security lifecycle review is a systematic and highly useful method for assessing and improving an organization’s cybersecurity. It is crucial for maintaining effective security strategies. It helps companies identify their vulnerabilities, review current plans, and be prepared to deal with threats.
What is a security lifecycle review?
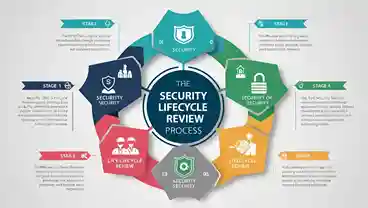
Security lifecycle review is a complete process. Under which the security of a system, network, or software is planned, executed, and monitored. It can be changed at any time throughout its life.
This review essentially ensures whether security is working as expected during design, development, use, and even in the final years of its life. The goal of this process is to always keep the system secure, defend it from threats, and implement quick fixes.
What is the purpose of Security Life Reviews?
A security lifecycle review evaluates an organization’s security measures and policies. It also examines the security practices of current processes. It identifies missing components and makes recommendations for improving them.
The review also provides organizations with very useful advice on how to effectively combat cyberattacks so that the company can be protected from these attacks.
Security Lifecycle Review What are the vulnerabilities of cyberattacks?
Here are concise points :
- Identifying weak passwords
- Checking outdated software
- Finding missing security updates
- Reviewing access controls
- Analyzing network settings
- Ensuring proper data backups
- Detecting a lack of monitoring tools
As a result, Security Lifecycle Review helps fix these risks early.
Key Phases in the Security Lifecycle Review
The security lifecycle review includes many essential steps that are critical to keeping businesses secure. Knowing and implementing these steps allows firms to effectively plan their security and ensures that they know how to implement these steps to address all potential threats.
Assessing Current Security Posture
Assessing the current security posture is a very important step. It involves reviewing all security procedures and policies.
Knowing and implementing these measures allows firms to effectively plan their security. And it ensures how to implement these measures to address all potential threats.
Companies use technology like Scan to identify security threats and identify weak security in their security setup, which helps them create better security plans in the future.
Implementing Security Measures
The next step is to implement security measures. Companies can create strategies after conducting a security check. These plans can include implementing new technology, making regulatory changes, or even training employees.
The sole purpose of each plan is to make the company safer. This helps a lot in avoiding security breaches and also ensures the safety of the workplace.
Benefits of Conducting a Security Lifecycle Review
Conducting a security lifecycle assessment benefits enterprises greatly. It improves their security. They can deal with new risks and follow rules more effectively.
Improved Risk Management
The main benefit of security lifecycle reviews is improved risk management. They can quickly detect security flaws and take various steps to recover them.
This makes it more difficult for hackers to break in. Being proactive ensures data security. It encourages everyone in the firm to be alert and agile.
Enhanced Regulatory Compliance
Regular security lifecycle reviews help with regulatory compliance in cybersecurity. Laws often change, but businesses and organizations remain on track.
These reviews go a long way in helping them comply with applicable laws and requirements. They also greatly reduce the likelihood of penalties. It is important to continue these reviews to maintain the build.
Common Challenges in the Security Lifecycle Review
During these assessments, organizations face several obstacles and difficulties. Acquiring a good cybersecurity resource is a huge challenge. Implementing these security measures becomes even more difficult if there is a limited financial system.
If these security measures are weak, cyber hackers take advantage of them, which is why upgrading them for strong security is very important. If we want to achieve the goal of long-term security protection, these financial challenges must also be overcome.
Resource Allocation Issues
Getting resources right is critical to effective cybersecurity. Not having enough money or people can result in not getting the correct security technology.
This can make systems vulnerable to threats. It is critical to focus on cybersecurity resources. This aids in risk mitigation and keeps systems safe from threats.
Resistance to Change
Managing change in security can be difficult. Employees may be hesitant to try new things for fear of taking on additional responsibility.
This can lead to slow adoption of new security tools. To combat this, communicate effectively, train personnel, and provide necessary guidance.
This creates a culture that embraces security changes and includes everyone.
Tools and Techniques for a Successful Security Lifecycle Review
Businesses must perform a comprehensive security lifecycle assessment using the right tools and techniques.
They facilitate operations and improve security. Cyber defenses can be strengthened with the aid of automation and threat intelligence.
Utilizing Automation Tools
Automation in cybersecurity reduces the amount of manual work required for security operations. Tools for security lifecycle review can do the following:
- Automatic vulnerability scanning
- Real-time monitoring of security warnings.
- Timely patch management
These tools aid in the rapid detection of dangers, resulting in a faster response to vulnerabilities. Moving to automation increases efficiency. It also allows experienced individuals to work on critical security plans.
Incorporating Threat Intelligence
Using threat intelligence effectively entails incorporating external data about risks to enhance security. Incorporating threat intelligence into the security lifecycle review helps businesses
- Receive real-time information about emerging dangers.
- Update security plans based on the current dangers.
- Improve how they manage incidents using reliable data.
This forward-thinking approach allows teams to stay one step ahead of threats. Combining threat intelligence with existing security measures results in a more effective security plan for the firm.
Best Practices for a Comprehensive Security Lifecycle Review
Keeping your security strong is essential for any organization. Regular security audits help identify flaws and stay ahead of threats. Getting everyone involved ensures that all perspectives are covered, resulting in improved security plans.
Regular Audits and Assessments
Regular inspections are the foundation of a solid security strategy. Set a schedule for these audits to ensure that your security is up-to-date. A thorough checkup may include:
- vulnerability scanning
- Threat Assessments
- Compliance checks with relevant regulations
Regular audits enable you to better address new dangers and comply with regulations.
Engaging Stakeholders
Getting everyone on board is critical for effective security. IT, legal, and HR teams all play a role. In this manner, you receive a complete view of what is required for security.
- Improved communication regarding security rules
- Improve teamwork on security tasks.
- Security goals that align with business plans.
Stakeholder involvement also promotes a security-conscious culture. It encourages everyone to contribute to maintaining high-security standards.
Documentation and Reporting
Maintaining detailed records is essential for security. It demonstrates your commitment to security and makes it easier to obey the guidelines. Good records should contain:
- Audit logs
- Plans to fix the found problems
- Updates for stakeholders.
This strategy aids in rule compliance and preparation for future checks. Doing a full security check helps keep your organization safe.
Security Lifecycle Review: Real-World Case Studies
Various case studies from the cyber world show how valuable and important a security lifecycle assessment can be.
Companies that use this methodology or principle benefit greatly from this added layer of security.
For example, large organizations and companies can identify their vulnerabilities, and by addressing them, they can develop better strategies for cyberattacks.
case studies
A bank, when faced with a cyberattack, discovered the flaws in its security assessments. It changed its entire strategy. They adopted a security strategy through a security lifecycle review. Similarly, an engineering firm revised its security practices to meet new requirements and developed a robust cybersecurity strategy.
This approach not only increased their security but also increased the trust of their customers. Eventually, the world’s largest institutions also used the security lifecycle review to fix weaknesses and build stronger, more trusted systems.
Security Lifecycle Review Strategy Results
The number of security incidents has decreased by 40 percent over the past two years. Companies of all sizes can benefit from these lessons. The outcomes of security lifecycle assessments highlight the significance of continual improvement.
| Organization Type | Security Review Outcome | Key Lessons Learned |
| Financial Institutions | 40% reduction in incidents | Invest in high-risk areas |
| Engineering Firms | Improved alignment with industry standards | Adapt protocols continuously |
| Healthcare Providers | Enhanced data protection measures | Prioritize patient data security |
These stories on Security Lifecycle Review highlight the need for regular checks. They also offer a guide for companies looking to strengthen their cybersecurity. By looking at these examples, businesses can find the best ways to do their security reviews.
Conclusion
Organizations must be vigilant against cyber threats at all times. Regular security checks should be conducted in today’s digital world. Regular security checks in today’s digital world help in risk management and enforcement of rules and regulations.
They always prepare business owners for the possibility of cyberattacks. That is why it is very important to review security practices, address security vulnerabilities, and use appropriate digital tools. This strategy enhances the reputation of any company.
It also protects digital assets and helps establish a strong position in the cyber world. That is why stakeholders should conduct regular checks, which make cyber defense strong and effective.